Services
Human Risk Service

Upskill your team from cyber zeroes to cyber heroes
People make mistakes
6 out of 7 of breaches involve human error.
People are targets
1 out of 3 of breaches involve phishing emails.
Stolen credentials
2 out of 3 of breaches involve stolen user credentials.
People can be your greatest weakness
Reduce incidents
Cybersecurity incidents are reduced by 70% by awareness training.
Reduce impacts
A modest investment in training has a 72% chance of reducing the impact of a cyber attack.
7-fold ROI
Even the least effective training programs have a 7-fold Return On Investment.
People can be your greatest strength
Free trial
You can try out the Human Risk Service for cost and obligation free for up to 3 people for 14 days.
For each person participating in the trial you’ll get:
- Dark web scan for stolen information.
- Gap analysis quiz and results.
- One training course module.
Demonstration of the phishing and policy management modules can be additionally arranged upon request.
Human Risk Service modules
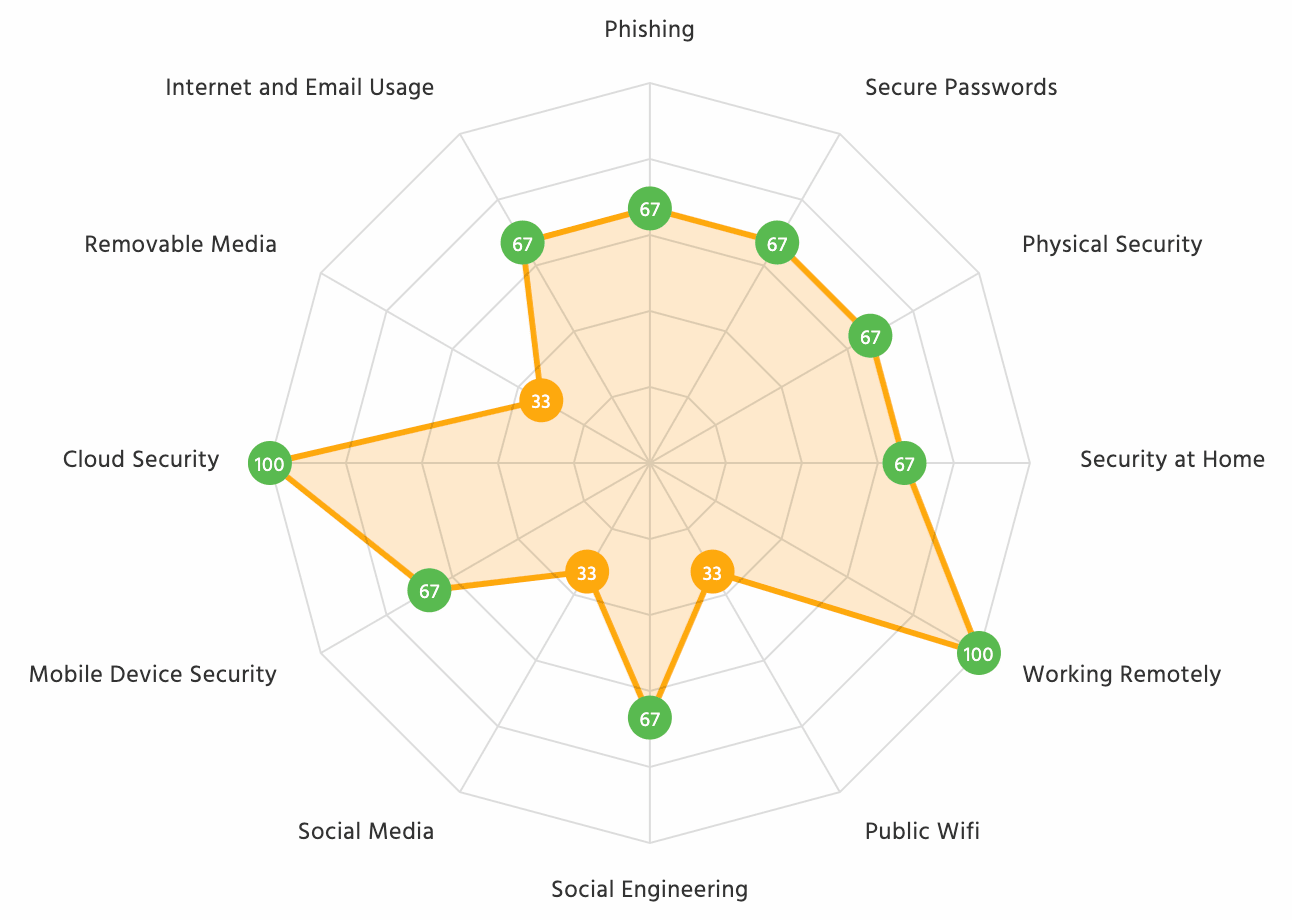
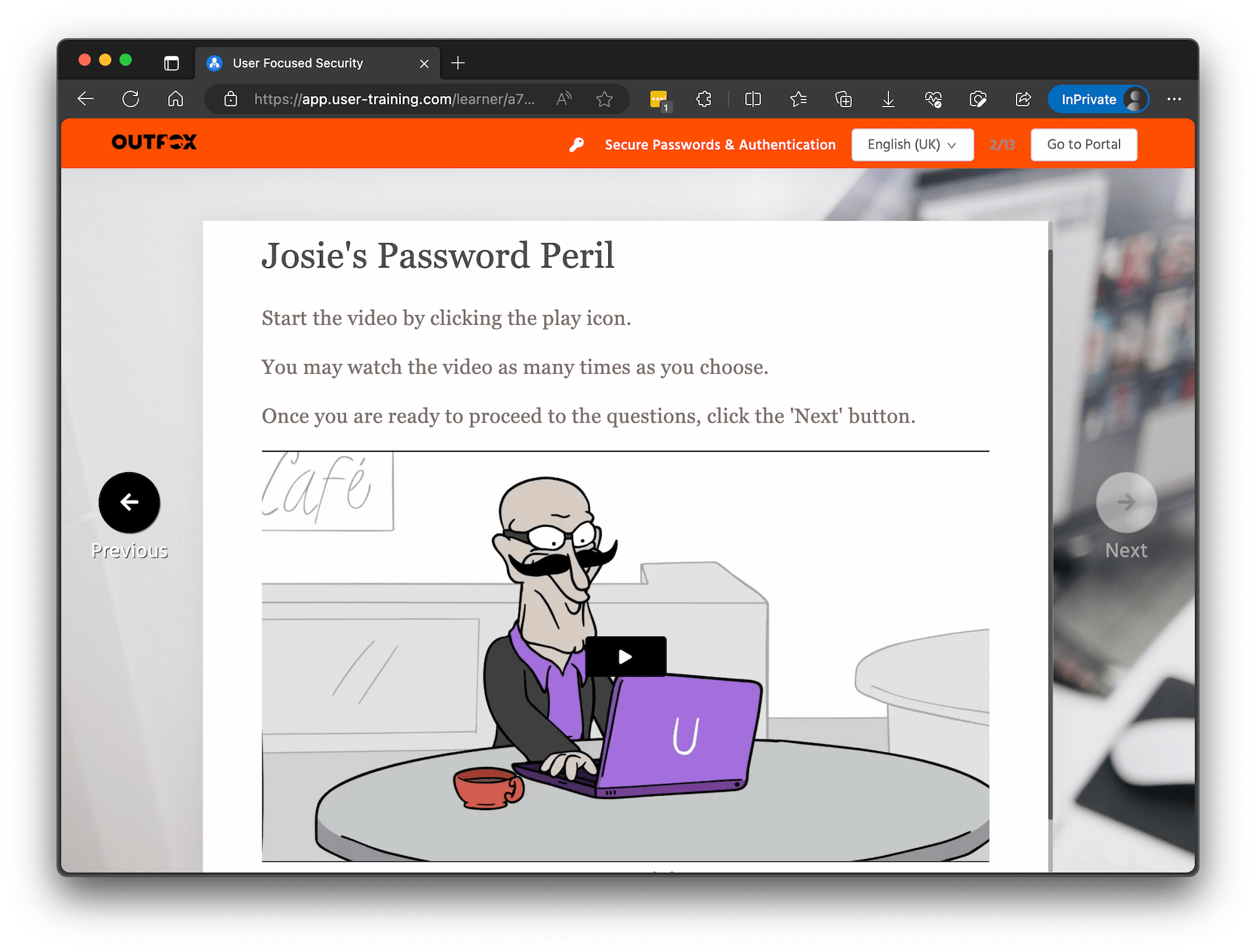
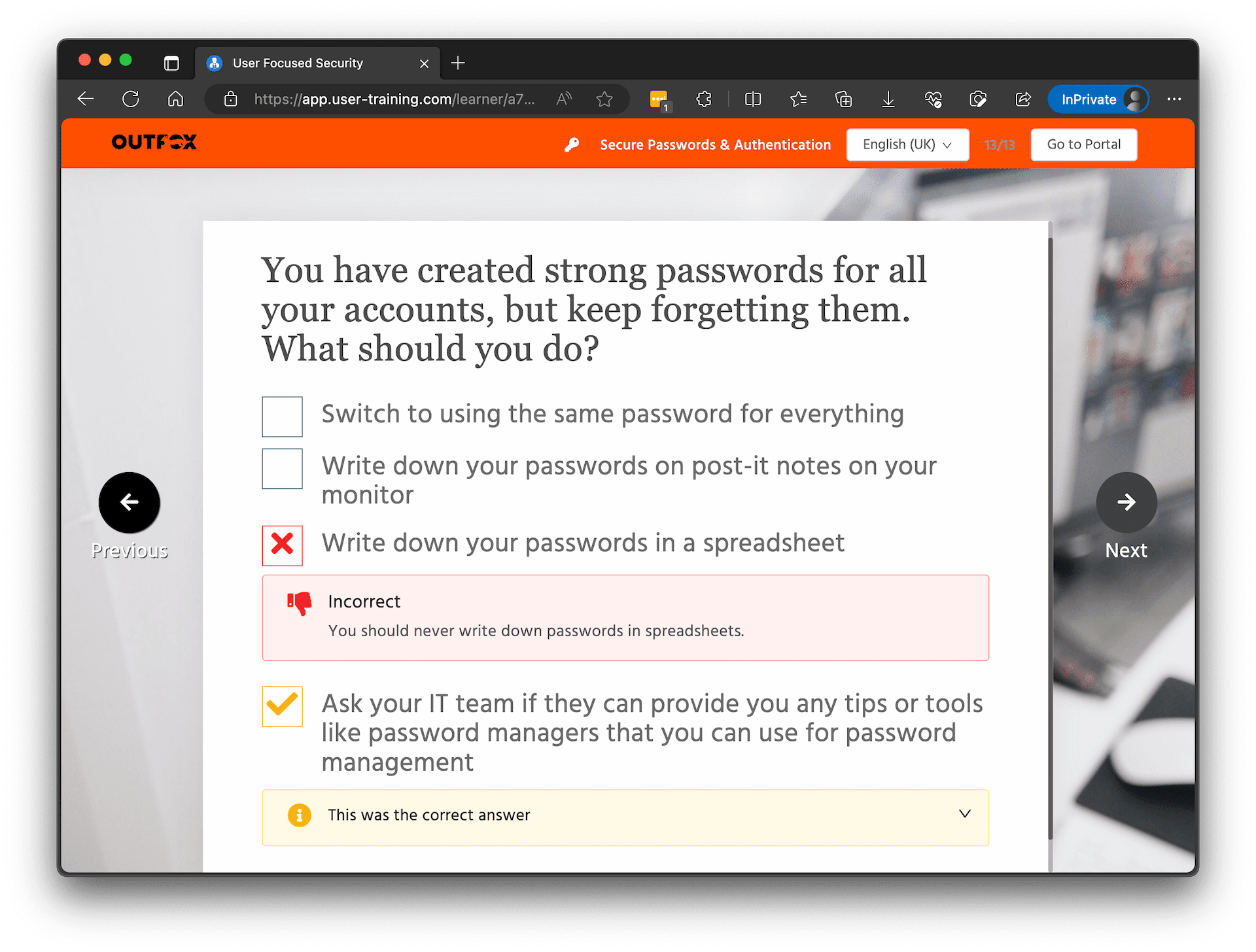
Security awareness training
Assess each person’s security knowledge gaps and automate regular training courses that tackle their unique risk areas.
- Individual-tailored training.
- Covers all essential topics.
- Automated reminders.
- Track user progress.
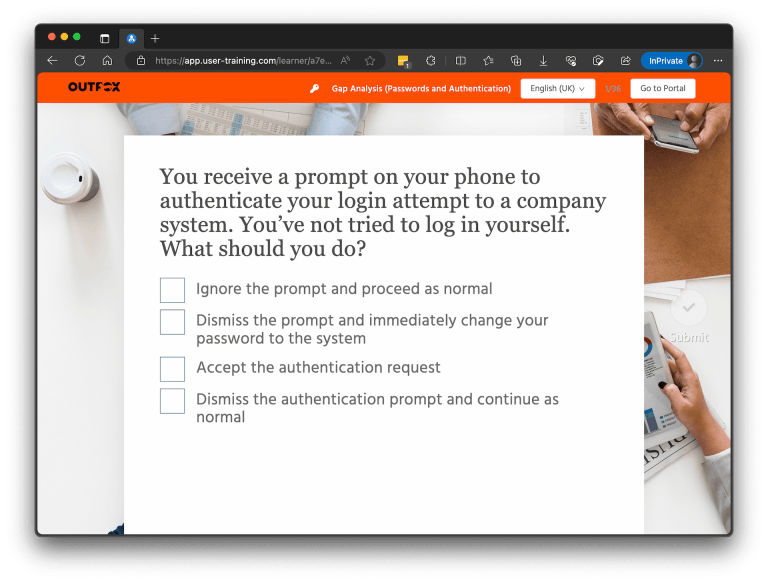
Simulated phishing
Periodic phishing simulations that assess your teams’ ongoing risk to a range of attack techniques.
- Identify at-risk team members.
- Educate users on threats.
- Tailored simulations.
- Instantly train at-risk team members.
Dark web monitoring
Continual dark web scanning for stolen credentials belonging to any of your team.
- Helps avoid targeted attacks.
- Details on who was breached.
- Details on what data was stolen.
- Enables pro-active action.
Policy management
Keep team members well-versed on security processes with easy policy management and trackable eSignatures.
- Standard or tailored templates.
- Tracks confirmation signatures.
- Automated reminders.
- Centralises your cyber policies.
How it works
Security awareness training
Simulated phishing
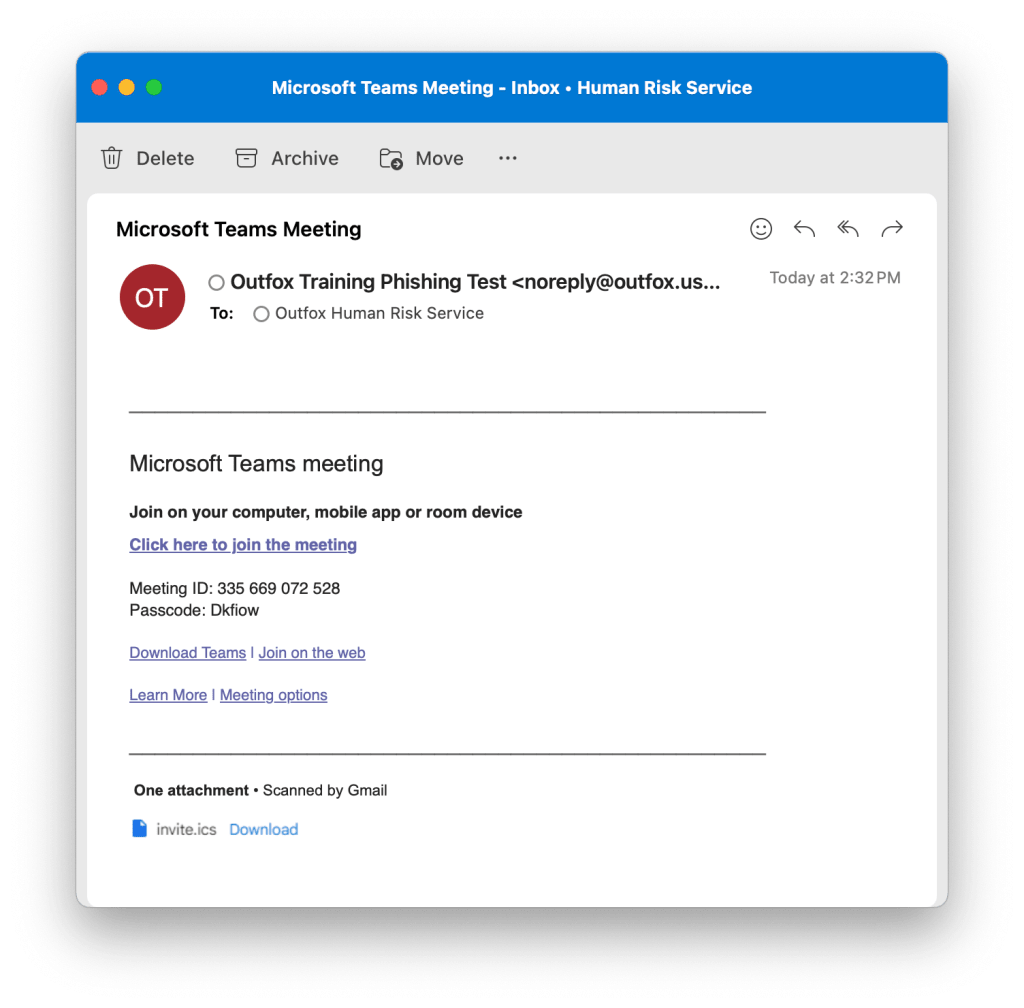
NB: requires the cooperation of your IT team and/or Managed Service Provider.
Simulated phishing messages can be sent to selected or all team members. A wide range of designs are available, or we can build one specifically for your organisation. The system records who opens the message, who clicks any links in it, and anyone who enters credentials.